¶ HTTPS/SSL
- Overview
- Domain configuration
- Certificates
- Testing and installing
- On-premise installation
- Access to the web page
¶ Overview
SSL Activation allows you to change your connection from "http" or "http/2" to "https" and vice versa.
SSL certification is important as it ensures that the data going from the user’s computer to the website stays secure and unreadable to any malicious intruders like hackers and identity thieves, as well as any other third parties.
Also, it is important to have SSL configured if you intend on using the Splynx mobile applications.
To change your connection from "http" to "https" you need to have a domain name.
If you already have a domain name and want to enable HTTPS, navigate to Config → Main → HTTPS/SSL:
¶ Domain configuration
There, you need to set your Common Name (main domain) and any additional domains:
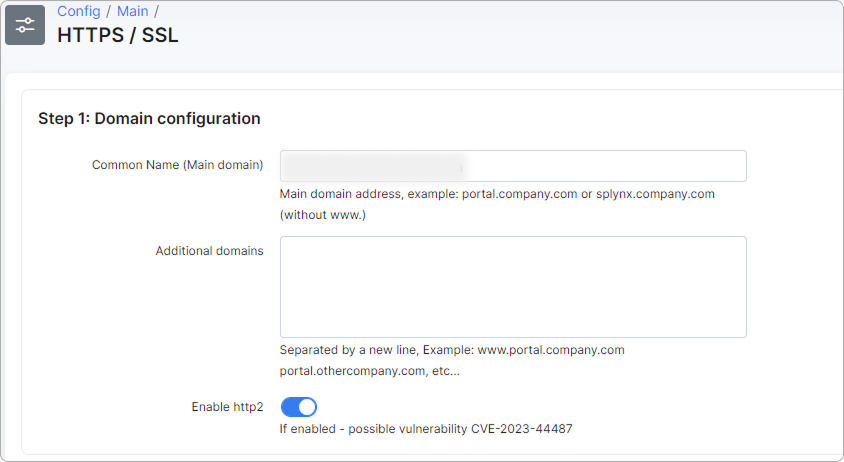
- Enable http2 - toggle the switch to enable the HTTP/2 connection.
If the HTTP/2 toggle is enabled, a potential vulnerability to be aware of is CVE-2023-44487.
Before adding a domain, make sure it has an A record and that the domain name is active and paid for with your domain registrar.
To verify that the A record is set up correctly, you can use the following command:
nslookup yourdomain.com
Example of executing this command:

Where:
yourdomain.com is the domain you want to add.
127.0.0.53 is your Domain Name Server (DNS).
192.124.249.6 is the public (no local) IP address of your Splynx.
Our cloud clients can choose the domain *.splynx.online and *.splynx.app for free.
For automatic renewal of SSL certificates, all domains must be resolved to your public IP address. If there is a problem with at least one domain, automatic renewal will not be launched for all domains. Manual activation of the new configuration will not be possible and you may lose access to the web page!
¶ Certificates
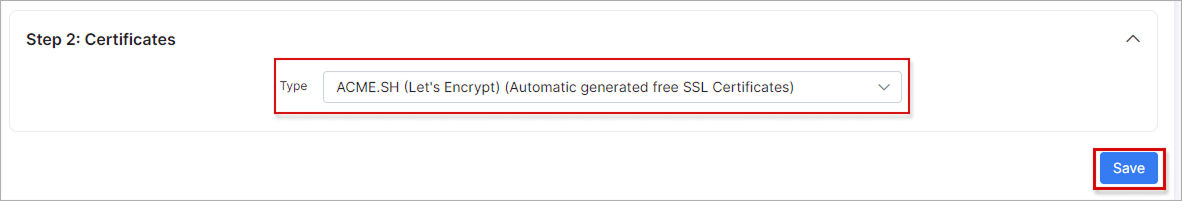
Now you need to choose whether you want the system to encrypt automatically by generating free SSL certificates, or if you prefer to set it up manually.
Automatically generated ACME.SH (Let’s Encrypt) certificates:
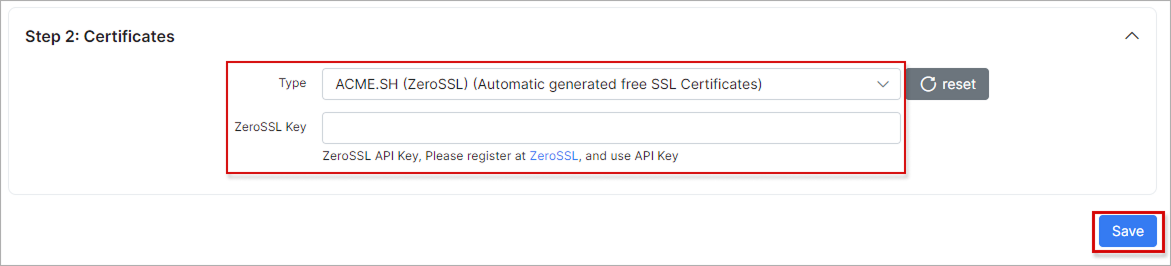
Automatically generated ACME.SH (ZeroSSL) certificates:
Manually added your own certificates:
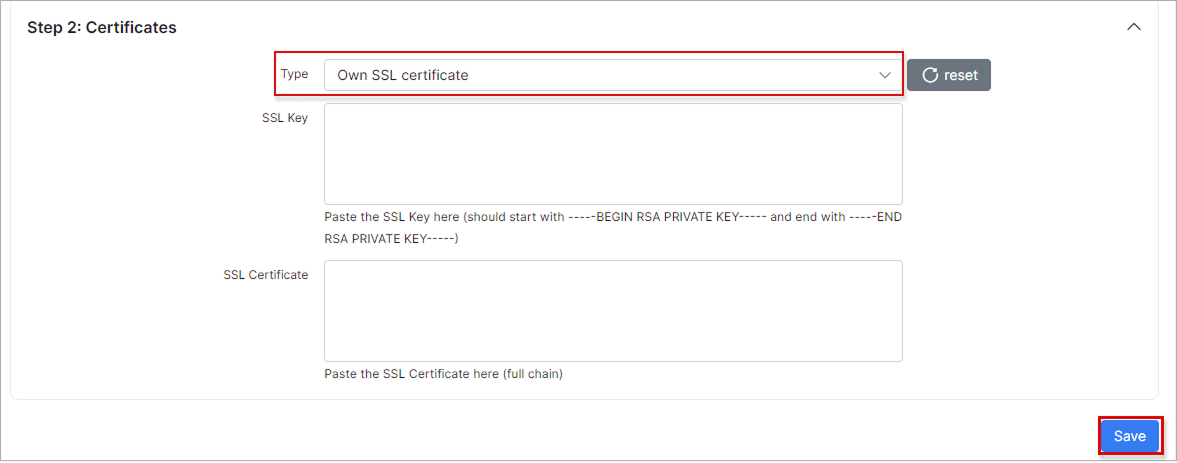
¶ Own SSL certificate
SSL certificate requirements:
- SSL certificate must include the full chain: primary (server) certificate, issuer certificate (intermediate CA) certificate and trusted root (root CA) certificate.
- The SSL certificate and its private key must be compatible.
¶ Full chain certificate
This is what a primary (server) certificate looks like:
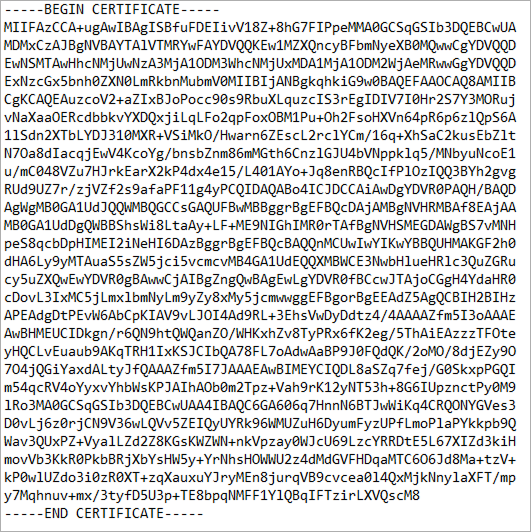
This is how an SSL certificate with a full chain should look like. These are 3 certificates in one file:

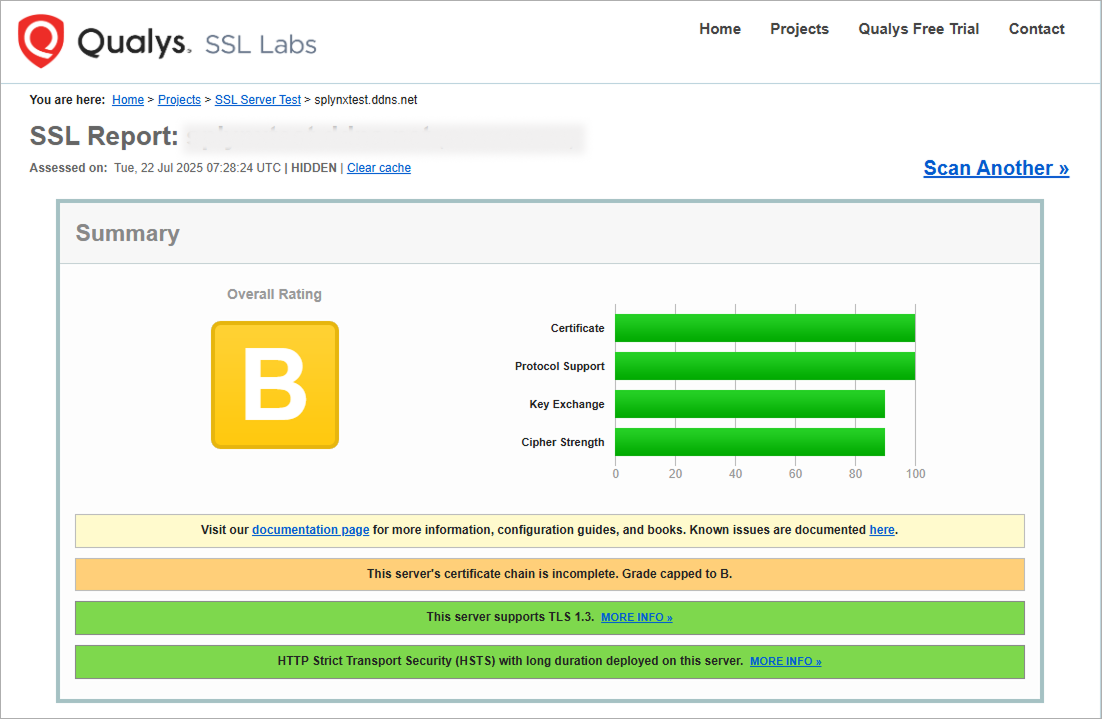
You must use a full chain certificate. SSL test website should show a rating of A or A+. If there is no full chain, then the test will show a rating of B and then add-ons and especially payment systems will not work with such certificates.
You can generate the full certificate chain yourself by using your SSL certificate issuer or an online service such as What's My Chain Cert?. Simply enter your primary (server) certificate to obtain the full chain.
¶ SSL key
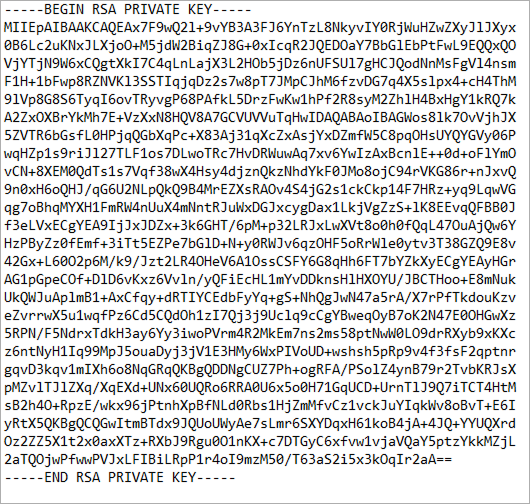
The SSL private key is used when generating a Certificate Signing Request (CSR), which is then submitted to a Certificate Authority (CA). The CSR includes the public key and identifying information, while the private key remains on the server and must be kept confidential - it is never transmitted.
This is an example of what an SSL private key looks like (the content has been altered for security; do not share your actual private key with anyone!):
There are several ways to check the compatibility of an SSL certificate and key:
- Modulo comparison (OpenSSL):
openssl x509 -noout -modulus -in cert.crt | openssl md5
openssl rsa -noout -modulus -in private.key | openssl md5
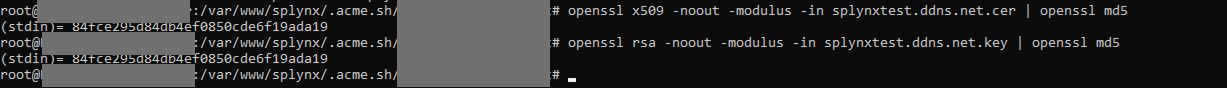
If the output matches, then the key and certificate are compatible
- Comparison by public key hash:
openssl x509 -noout -pubkey -in cert.crt | openssl pkey -pubin -outform der | openssl dgst -sha256
openssl rsa -in private.key -pubout -outform der | openssl dgst -sha256
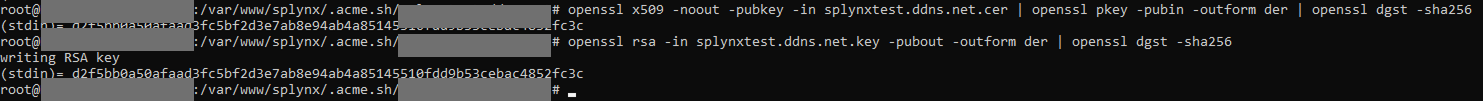
If the hashes match, this confirms the pair's correspondence
- Third-party services for comparing SSL certificate and key, for example (use only if other methods are not available, since you are transferring the SSL key to third parties):
https://www.sslshopper.com/certificate-key-matcher.html
https://www.leaderssl.com/tools/certificate_key_matcher
¶ Testing and installing
If you choose the "Let's Encrypt" or "ZeroSSL" option, click Validate config to complete the validation. Then, click Activate new config to finalize the setup. Afterward, wait a few minutes for the configuration to be validated and applied.
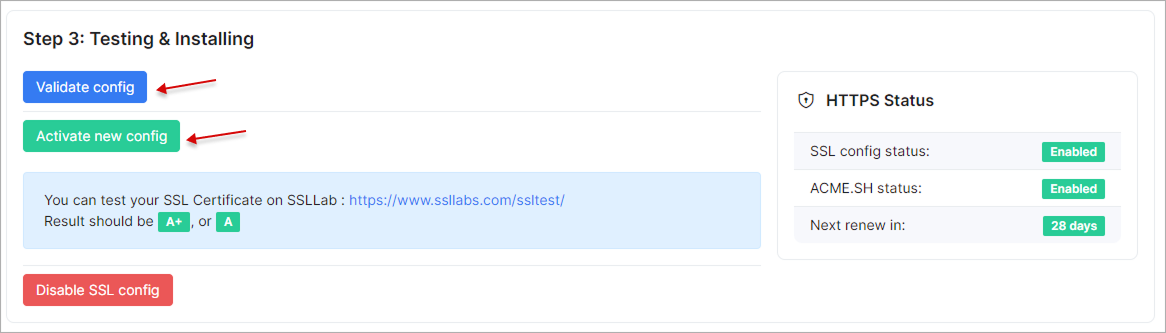
If you choose the "Own SSL certificate" option, you have to manually configure your SSL Key and SSL Certificate. Then, click Validate config to complete the validation. After that, click Activate new config, and wait a few minutes for the configuration to be validated and applied.
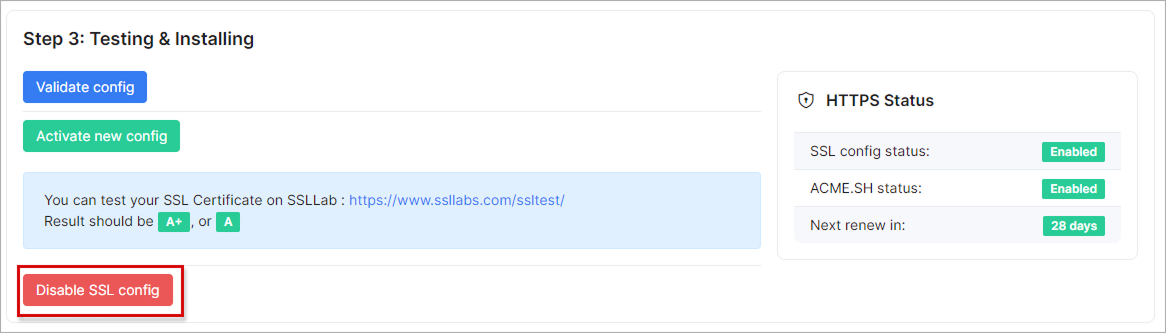
To revert to HTTP, click the Disable SSL config button and clear your browser cache:
¶ SSL Certificate test
SSL Server Test by ssllabs.com is an online tool for checking the security and proper configuration of the SSL/TLS certificate on your server. SSL Labs' SSL Server Test assigns ratings in the form of letter grades that reflect the overall security level of a server's SSL/TLS configuration.
Thus, this test helps to understand how secure your server is, whether SSL is configured correctly and whether it meets modern security requirements.
Here's how automatic Type ACME.SH (Let's Encrypt) certificates are rated:
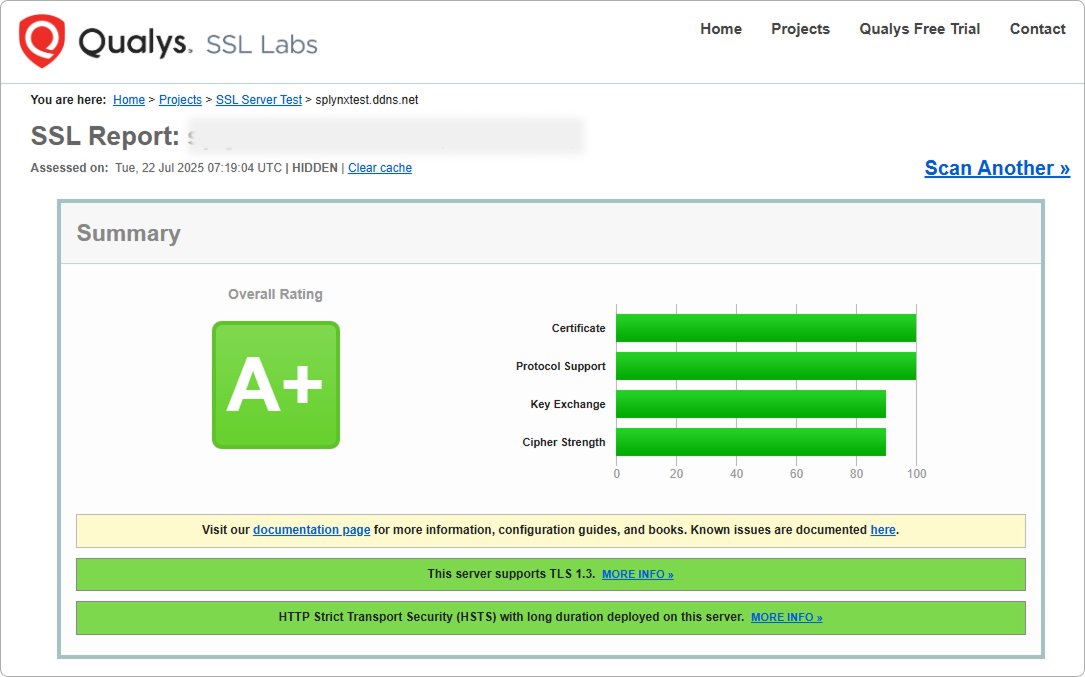
Own certificate without full chain:
¶ On-premise installation
To activate an SSL certificate on on-premise server, in particular ACME.SH (Let's Encrypt), the following requirements must be met:
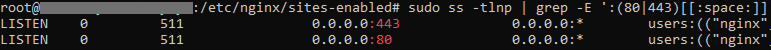
- TCP 80 and 443 ports must be free, or used by nginx services. Must be listened to by all hosts (0.0.0.0):
- TCP 80 and 443 ports should not be blocked by firewall rules
- TCP ports 80 and 443 should be accessible from the internet.
 To do this, it is enough for the network interface to have a public IP address. Or in the case of using NAT, the network gateway must have destination NAT rules that forward TCP ports 80 and 443 from the internet side to the Splynx server.
To do this, it is enough for the network interface to have a public IP address. Or in the case of using NAT, the network gateway must have destination NAT rules that forward TCP ports 80 and 443 from the internet side to the Splynx server.
Console commands:
Checking ports on the server:
sudo ss -tlnp | grep -E ':(80|443)[[:space:]]'
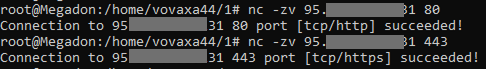
Checking the port remotely, where 1.1.1.1 is public (no local) IP address of Splynx server:
nc -zv 1.1.1.1 80
nc -zv 1.1.1.1 443
Checking HTTPS remotely via console:
curl -L https://splynxtest.ddns.net
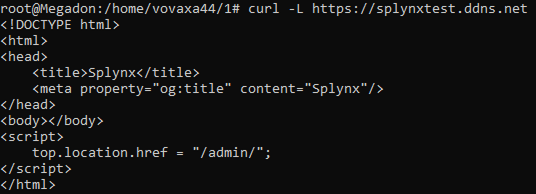
HTTPS activation with the new ACME.SH (Let's Encrypt) certificate:
/var/www/splynx/.acme.sh/acme.sh --server letsencrypt --cron --home /var/www/splynx/.acme.sh --force
¶ Access to the web page
In normal cases, the HTTPS protocol and domain name are used to access the Splynx web page:
https://youdomain.com/admin
However, in cases where SSL activation was not correct, there are problems with the certificate or domain and you have lost access to this URL, you can try other variants:
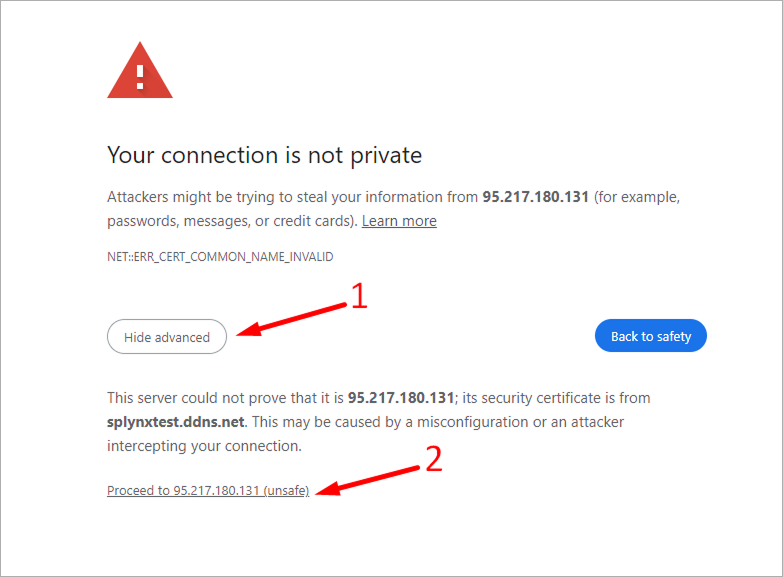
https://95.217.180.121/admin
https://192.168.50.5/admin
http://95.217.180.121/admin
http://192.168.50.5/admin
Where:
95.217.180.121 is public IP address of your Splynx
192.168.50.5 is local IP address of your Splynx (available only via local network)
If HTTPS is activated (even with a problematic SSL certificate), an automatic redirect from HTTP to HTTPS occurs.
When logging into the page, you may see the following error, but you can ignore it and forcefully go to the page: