¶ MikroTik API
- Overview
- Size
- API
- Accounting
- Router accounting options
- Simple shaping
- PCQ shaping
- PPP secrets
- IP firewall filter and DHCP
- Force API configuration
¶ Overview
To configure MikroTik API navigate to Config → Networking → MikroTik API.
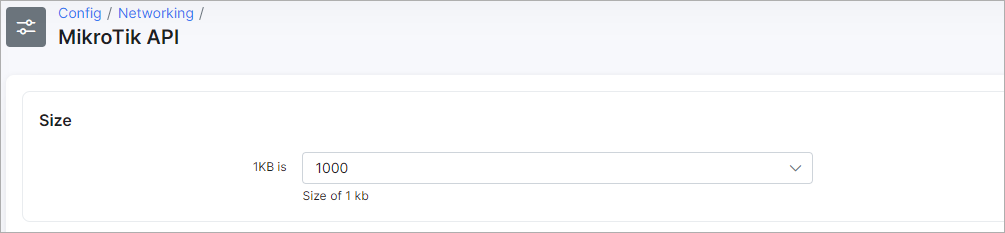
¶ Size
Here we have to specify how many bytes is in 1KB in Splynx, available options are 1000 or 1024 bytes.
¶ API
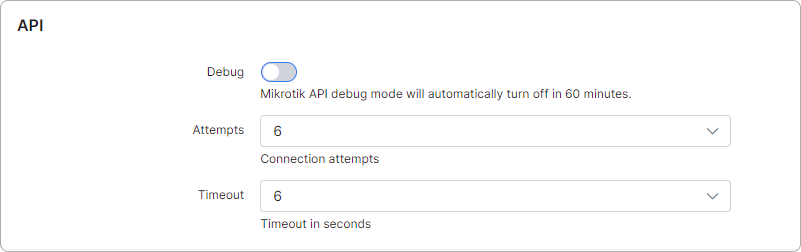
-
Debug - enables/disables API debug log (under /var/www/splynx/logs/cron/mikrotik.log). Recommended only for testing/debug purposes. The Mikrotik API debug mode will automatically turn off in 60 minutes;
-
Attempts - select connection attempts (1-10);
-
Timeout - select timeout in seconds.
¶ Accounting
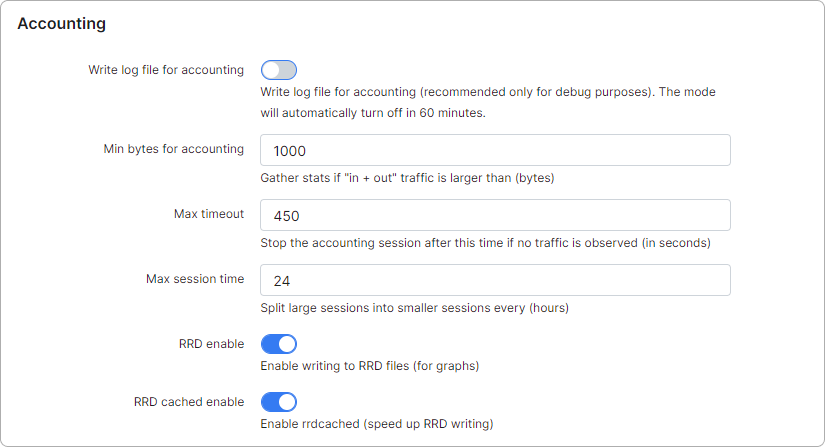
-
Write log file for accounting - enables/disables accounting log (under /var/www/splynx/logs/cron/accounting.log). Recommended only for testing/debug purposes (the mode will automatically turn off in 60 minutes);
-
Min bytes for accounting - gather stats if "in + out" traffic is larger than (bytes);
-
Max timeout - stops the accounting session after this time if no traffic is recorded during the specified period of time (in seconds);
-
Max session time - divides large sessions into smaller sessions every (hours);
-
RRD enable - enables/disables writing to RRD files (for graphs);
-
RRD cached enable - enables/disables RRD cache (speeds up RRD writing).
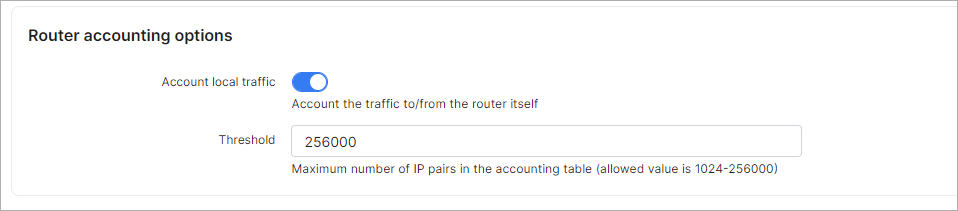
¶ Router accounting options
-
Account local traffic - enables/disables accounting of the traffic to/from the router itself;
-
Threshold - maximum number of IP pairs in the accounting table (allowed value is 1024-256000).
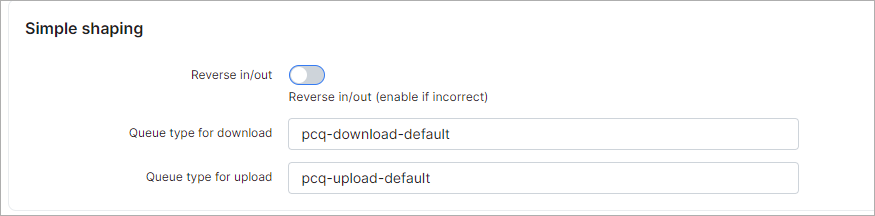
¶ Simple shaping
- Reverse in/out - enable this if you want to change upload by download and vice versa;
- Queue type for download - set the queue download type;
- Queue type for upload - set the queue upload type.
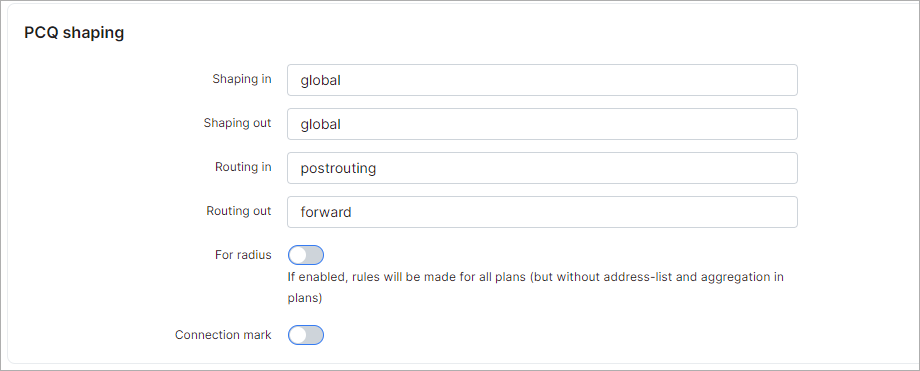
¶ PCQ shaping
- Shaping in - chain where the rules are created;
- Shaping out - chain where the rules are created;
- Routing in - set the type of routing in;
- Routing out - set the type of routing out;
- For radius - if yes, rules will be created for all plans (but without address-list, and without aggregation in plans);
- Connection mark - enables a connection mark.
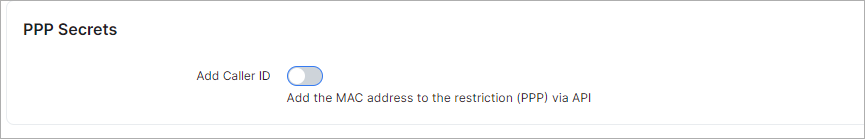
¶ PPP secrets
- Add caller ID - enables/disables adding the MAC address to the restriction (PPP) via API;
¶ IP firewall filter and DHCP
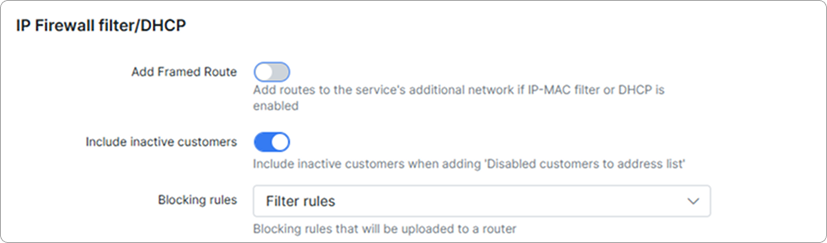
-
Add framed route - enables/disables adding routes to the service's additional network field if IP-MAC filter or DHCP is enabled;
-
Include inactive customers - enable this toggle to include inactive customers when adding 'Disabled customers to address list';
-
Blocking rules - select blocking rules that will be uploaded to a router: Filter rules or DNS blocking rules.
Only IP/IPv6 firewall blocking rules without comments are allowed; firewall address list entries are not supported in this field.
- Filter rules - List of firewall filter rules that will be uploaded to the MikroTik router.
Use{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}for allowed resources' address list name and{{SPLYNX_IP_ADDRESS}}for the Splynx IP address:
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=SpLBL_blocked
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=SpLBL_new
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=SpLBL_disabled
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=Reject_0
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=Reject_1
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=Reject_2
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=Reject_3
/ip firewall filter add chain=forward action=jump jump-target=splynx-blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} src-address-list=Reject_4
/ip firewall filter add chain=splynx-blocked action=accept protocol=udp dst-port=53 dst-limit=2,0,src-address/1m40s
/ip firewall filter add chain=splynx-blocked action=accept protocol=tcp dst-port=80,443,8101,8102,8103,8104 dst-address={{SPLYNX_IP_ADDRESS}}
/ip firewall filter add chain=splynx-blocked action=reject reject-with=icmp-admin-prohibited dst-limit=10,0,src-address/1m40s
/ip firewall filter add chain=splynx-blocked action=drop
- DNS blocking rules - List of firewall filter and NAT rules that will be uploaded to a router. Use
{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}for allowed resources Address list name and{{SPLYNX_IP_ADDRESS}}for Splynx IP address:
NAT rules are required for DNS blocking.
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address=10.250.64.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address=10.250.96.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address=10.250.128.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address=10.250.160.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address=10.250.192.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=Reject_0 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=Reject_1 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=Reject_2 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=Reject_3 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=Reject_4 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=SpLBL_blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=SpLBL_disabled dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall filter add chain=forward action=reject reject-with=icmp-admin-prohibited src-address-list=SpLBL_new dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}}
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_0 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_0 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_1 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_1 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_2 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_2 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_3 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_3 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_4 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=Reject_4 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=SpLBL_blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=SpLBL_blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=SpLBL_disabled dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=SpLBL_disabled dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=SpLBL_new dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=80
/ip firewall nat add action=dst-nat chain=dstnat to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=443 protocol=tcp src-address-list=SpLBL_new dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} dst-port=443
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address=10.250.64.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address=10.250.64.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address=10.250.96.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address=10.250.96.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address=10.250.128.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address=10.250.128.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address=10.250.160.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address=10.250.160.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address=10.250.192.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address=10.250.192.0/20 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}}
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=Reject_0 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=Reject_0 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=Reject_1 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=Reject_1 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=Reject_2 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=Reject_2 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=Reject_3 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=Reject_3 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=Reject_4 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=Reject_4 dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=SpLBL_blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=SpLBL_blocked dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=SpLBL_disabled dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=SpLBL_disabled dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=tcp src-address-list=SpLBL_new dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
/ip firewall nat add action=dst-nat chain=dstnat dst-port=53 protocol=udp src-address-list=SpLBL_new dst-address-list=!{{SPLYNX_ALLOWED_RESOURCES_ADDRESS_LIST}} to-addresses={{SPLYNX_IP_ADDRESS}} to-ports=53
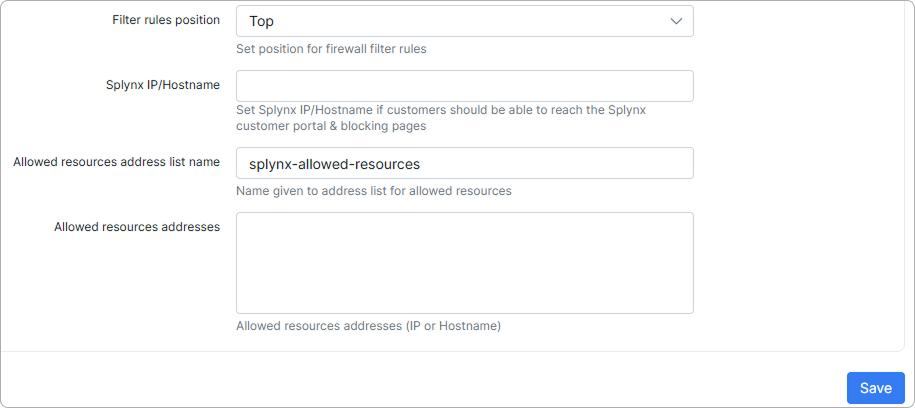
-
Filter rules position - select the position for firewall filter rules. Available options are: keeps current, top, bottom;
-
Splynx IP/Hostname - set Splynx IP/Hostname if customers should be able to reach the Splynx customer portal & blocking pages;
-
Allowed resources address list name - name for the address list for allowed resources;
-
Allowed resources addresses - allowed resources addresses (IP or Hostname).
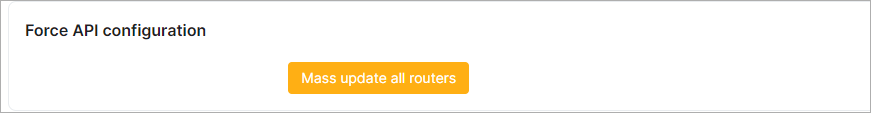
¶ Force API configuration
Click on Mass update all routers if you want to apply new Mikrotik API configurations.